The recognition of the top five infamous Cyber Attacks and the solutions for their extermination.
The need for high-tech rectification for the sake of eliminating Cyber Attacks is indeed today’s tragedy but it all comes down to mandatory shielding.
The Corporate World has been plagued by the Dark Web on the Cyber battlefield for far too long, subsequently, they intensely distress and wear out the cybersecurity channels implemented by various enterprises.
The passion although, quite differs; from a vast range of money to data theft, tarnishing renowned personas, corporate interference, social and personal gains, the replication of sensitive information, and lastly, exposing corporate cultures to their competition.
Fortunately, a keyboard for us is equivalent to an arrow for an archer.
Hunting Down and Mitigating Cybercrime!
The overpopulation of Cybercrime has denominated the progress of the corporate world as a whole. Despite prevention and protection techniques being implemented by enterprises worldwide, Cyberattacks’ modifications and adaption to cybersecurity methods have led to major irremediable breakdowns.
Financial Damages Caused by a Cyberattack,
Specific Tangible and Intangible Costs will incur to any sole individual or corporate organization as an impact of being Cyberattacked as listed below;
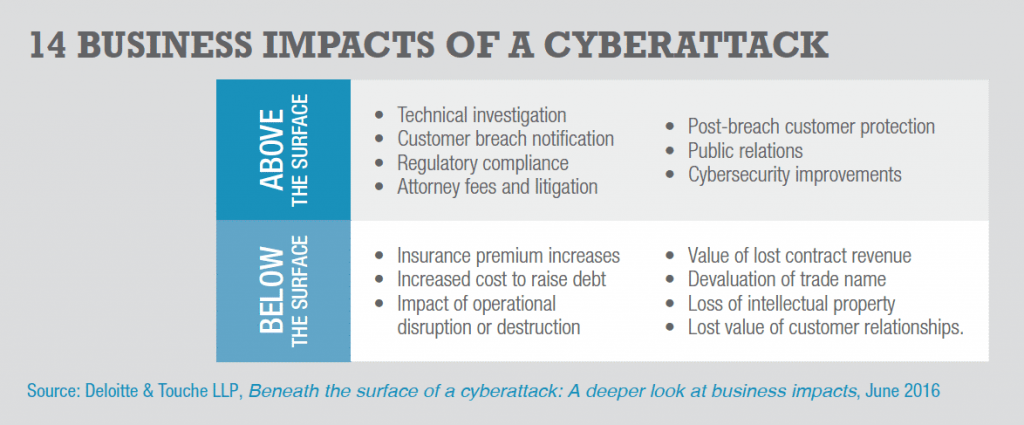
To evade these brutal consequences of a Cyberattack, irrespective of being above or below the surface, a significant factor would render to the understanding of the characteristics of these attacks. To support the latter, worthwhile avoidance tips in relation to various categories of Cyberattacks will be stated in the following.
Phishing Attacks – Invitation to Destruction
The uniformity of social engineering combined with high-tech duplicity used to carry out the theft of users’ sensitive information is identified as Phishing. Having the motive of data theft, hackers from the dark web dispatch bugged emails to an abundance of the target population. The latter may view them as innocent and resourceful while a single tap can lead to the penetration of their viruses into the enterprise’s cybersecurity walls, eventually cavitating them.
Even the most established of enterprises find themselves vulnerable at the hands of hackers. During 2013-2015, a phishing streak led to Facebook and Google suffering massive losses of $100 million.
Unfortunately, updated variants of phishing attacks have also come into existence as explained in the following:
Spear Phishing – The Art of Impersonation
While traditional Phishing techniques revolve more around the mass user population, Spear Phishing stands out to be more sophisticated and targeted in its manners. The latter indicates to their aim is a more specific individual or organization. The convincing yet hoax authenticity of their directed emails can allow hackers to gain access to their prey regardless of the latter’s cybersecurity sturdiness. All entities inclusive of private and public organizations have found themselves suffering endlessly at the hands of Spear Phishing.
Pharming – Stranger Danger!
Ironically, irrespective of how old we get, our mom’s infamous idiom “Stranger Danger”, also applies when we enter ourselves in the Tech World.
Pharming is a form of Phishing that doesn’t hunt the prey itself but appears friendly enough for them to trust them on their own. The creation of counterfeit or hoax websites to deceive entities into giving up their private and sensitive information; typically credit card info, their address, passwords to private accounts, and immeasurably more.
Whaling — Catching The Biggest Fish In The Sea
A form of phishing that is extremely specifically sophisticated in its techniques renders it to be Whaling. Like whales in the sea, fewer quantitatively, but bestowed with tremendous value in themselves, Chief Executive Officers are the whales of the corporate world. The majority of fishermen throw a fishnet into the water with the intent of capturing as many fish as possible. However, a predator aiming for a whale only will be better equipped, more aware, and skilled enough to do so.
Clicking on a link from the dark web can lead to hackers accessing direly sensitive information that a CEO may be in possession of. The latter could provide them access to not only their financial credentials but business secrets and plans.
Email Phishing – Unsolicited E-Messages
Venomous E-Messages are so intricately designed and well laid out that it’s hard for a daily user to determine how poisonous they can be when came in contact. Even when backed up with the protection of a Cybersecurity wall, hackers can exploit naïve users by a vast spread of deceitful information that will help facilitate the fulfillment of their objective. The latter being stolen sensitive credentials.
Pointers For Counteraction – Time To Fight Back!
Safeguard your credentials and data with the further stated threat elimination techniques :
- Became familiar with signs of counterfeit emails e.g. spelling errors, and empty links.
- Download Anti-Phishing software on all your devices.
- Never click on redirected or forwarded links from unauthorized sources.
- Avail Devflovv’s unmatchable source facilities available to retaliate against all forms of Phishing Attacks.
- Educate employees and yourself about the nature of these Phishing Attacks and test them on their knowledge to indirectly convey the dire need for protection and the gravity of these attacks.
- Recruit exclusive DNS services.
- Corroborate a site’s authenticity by being vigilant in observing the presence of a lock icon and HTTPS in the beginning.

